A Tutorial for Ubuntu 9.04
About a month ago, I wrote
an introduction to using the Dropbox service to backup your important data. Any data that you backup with Dropbox is encrypted and uploaded to
Amazon’s S3 service. Unfortunately, it is the people who run Dropbox that hold the keys used to perform this encryption. Regardless of how great the service is, storing your files with Dropbox involves placing your trust in the people who currently run the Dropbox service, as well as all of the people who will ever run Dropbox in the future. This is an unacceptable risk for many people and many kinds of data.
Thankfully, there is a strategy that can greatly reduce the risk. It is possible to automatically encrypt your files, and then use Dropbox to backup the encrypted versions. This means that you can have your cake and eat it too! Dropbox provides a convenient backup strategy so that your files can’t be lost due to the theft or destruction of your laptop. The encryption software ensures that your files can’t be accessed by anyone who works for Dropbox, or any hackers that might have infiltrated the servers that Dropbox uses.
If you’re using Ubuntu, the software that you need is free, and it isn’t especially difficult to set up. Please note that this tutorial will require you to use the command-line and edit some configuration files. Don’t be afraid! I will try to explain the process in a step-by-step fashion. If you’re just getting started with Linux, this project might help you get used to the command-line a little bit.
(Note: this has been tested on Ubuntu 9.04 only; I am not confident that these exact instructions will work on older versions of Ubuntu.)
Part 1: Set Up Dropbox
The rest of this tutorial will assume that you have the Dropbox client software installed on your computer. Detailed instructions can be found in the “Installing Dropbox” section of
my previous post on the Dropbox service. When you have finished following those instructions, proceed with Part 2.
Part 2: Removing Unencrypted Data
This section only applies if you have already used Dropbox to store some data that you would now like to encrypt. If you have never stored any files in your Dropbox, skip ahead to Part 3.
The first step is to take all of the contents of your Dropbox folder and back them up somewhere else. The following command will copy everything in your Dropbox into a folder named “DropboxBackup” (open a Terminal by clicking Applications -> Accessories -> Terminal):
1 | cp -r ~/Dropbox ~/DropboxBackup |
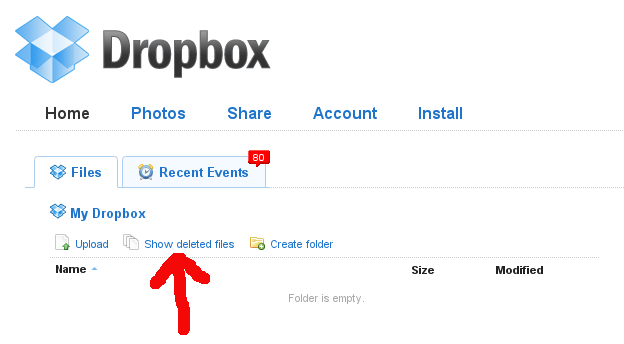
Once everything has finished copying, it might even be a good idea to burn this folder to a CD, just to be safe. Now we can proceed to delete all of the files in the Dropbox folder. Open your Dropbox folder in the file manager by left-clicking on the Dropbox applet in the top-right. Click the “View” menu and ensure that “Show Hidden Files” is checked. Next, select all the files and hit the Delete key. Dropbox should begin synchronizing the changes. Unfortunately, once the synchronization completes, nothing will have been actually deleted yet; the files will simply be marked as deleted, but it will still be possible to recover them.
In order to actually get rid of the files, open your web browser, go to
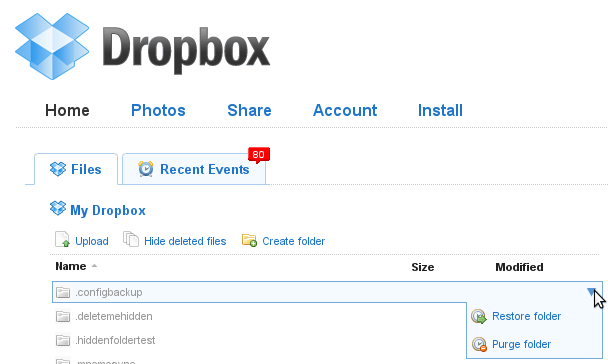
www.getdropbox.com and log in. Click the “Show deleted files” button.
For each deleted file, select the “Purge” option.
Part 3: Reconfiguring the Dropbox Client
The encryption software that will allow you to secure your Dropbox is called “
EncFS“. It works by creating a folder in which to store an encrypted version of each of your files and folders, and then making the unencrypted names and content available in a different folder. When we are finished with this tutorial, the folder containing the encrypted files will be stored within the Dropbox folder, and will therefore be automatically backed-up. Since we don’t want to accidentally store any non-encrypted files in the Dropbox folder, we will move the real Dropbox folder to a hidden location.
Right-click on the Dropbox applet and choose “Preferences…”; under the “Main” tab, click “Move…”:
Move to your Home Folder and click the “Create Folder” button. Give the new folder the name “.dropbox_encrypted” and click “Open”. Close the preferences window. On to Part 4!
Part 4: Configure an Encrypted Filesystem with EncFS
Now we’re ready to actually do some encrypting. In the commands that follow, you will need to substitute your username in place of <>. Open a terminal and enter these commands:
1 | sudo apt-get install encfs libpam-mount |
2 | sudo adduser <<yourusername>> fuse |
(As an example, if your username is “pragmattica”, then the command just above should be sudo adduser pragmattica fuse)
Now you need to log out and log back in again before continuing. Next, run this command:
1 | encfs ~/.dropbox_encrypted/Dropbox/encrypted ~/Dropbox |
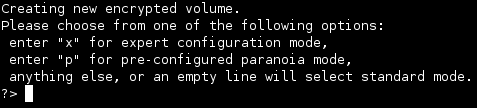
The encryption software will ask you a series of questions. Enter the following responses:
- Enter ‘y’ to create the encrypted directory
- Enter ‘y’ to create the unencrypted directory
- Enter ‘x’ to choose expert Mode (I experimented with the pre-configured paranoia mode, but encountered performance issues)
- Enter ’1′ to use the AES cipher algorithm
- Enter ’256′ for the key size
- Enter ’1024′ for the block size
- Enter ’1′ for block filename encoding
- Enter ‘y’ for filename initialization vector chaining
- Enter ‘n’ for per-file initialization vectors
- Enter ‘n’ for block authentication code headers
- Enter ‘y’ for file-hole pass-through
- Enter and repeat the password for the new encrypted filesystem; in order for the next part of the tutorial to work, the password must be the exact same password that you use to log in to your computer after turning it on
I’m probably not telling you anything that you don’t already know, so I’ll be brief. A good password should consist of upper and lower-case letters, numbers and punctuation characters. It should be fairly random looking, and pretty long; more than 20 characters, preferably.
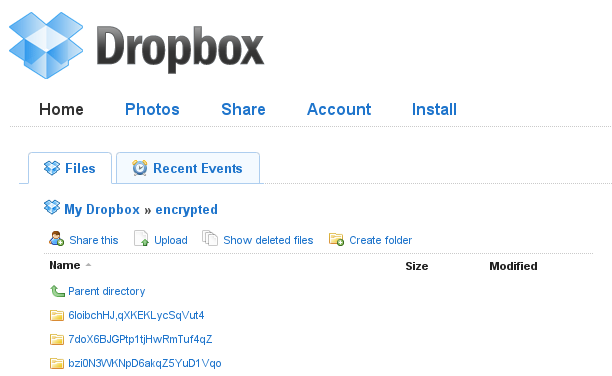
You can now begin copying files into your
/home/<>/Dropboxdirectory. The files that you copy in should be encrypted and backed-up by Dropbox. If you log in to the
Dropbox website, all of the saved files should have meaningless gibberish names and encrypted contents.
Part 5: Use pam_mount to Automatically Mount Your Encrypted Filesystem
At this point, it would be possible to use the command-line to manually mount your encrypted filesystem every time you turn your computer on, but we can do better. A program named “
pam_mount” can automatically mount the filesystem as soon as you log in. Open a terminal and enter this command:
1 | sudo gedit /etc/security/pam_mount.conf.xml |
Look for the line:
Right beneath that line, add this new line:
1 | <volume user="<>" fstype="fuse" path="encfs#/home/<<yourusername>>/.dropbox_encrypted/Dropbox/encrypted" mountpoint="/home/<<yourusername>>/Dropbox" /> |
To eliminate a harmless but annoying error message, use “sudo gedit” as above to edit the /etc/pam.d/common-pammount and /etc/pam.d/common-auth files and eliminate all occurrances of the word use_first_pass.
The next time you turn your computer on and log in, you should be able to go to your new /home/<>/Dropbox folder and see the unencrypted versions of your important files. Unfortunately, this new folder won’t display the little status icons on each file, so you’ll have to keep an eye on the Dropbox applet to know when the synchronization of your files is in progress or complete. I think that this is a very reasonable sacrifice for the additional security.
One last tip: the icon for your secure Dropbox folder is now the same as for every other folder. To give that folder some visual distinction, it’s possible to change its icon. Right-click on the folder and select “Properties”. Click on the little Folder icon in the top-left of the properties dialog box and set the icon to/usr/share/icons/hicolor/64×64/apps/dropbox.png.
Security Considerations
As an added benefit, this strategy will also provide a little protection against your information being compromised by someone who steals your laptop. The reason this only provides a little protection is due to the tendency of modern operating systems and software to scatter bits of information about while working. The actual files themselves are encrypted, but unencrypted bits of the files might still end up lying around in temporary files or the swap partition. An attacker with enough skill and determination would be able to find those. Still, it’s better than nothing.
This is probably going to be my last security-related post for a while. I’ve been going through a security phase lately, but I’m feeling pretty good about the precautions that I now have in place. Next post, I will be back to my regularly scheduled programming topics. As always, if you have any problems with anything in the tutorial, just leave a comment. I’m always happy to help.